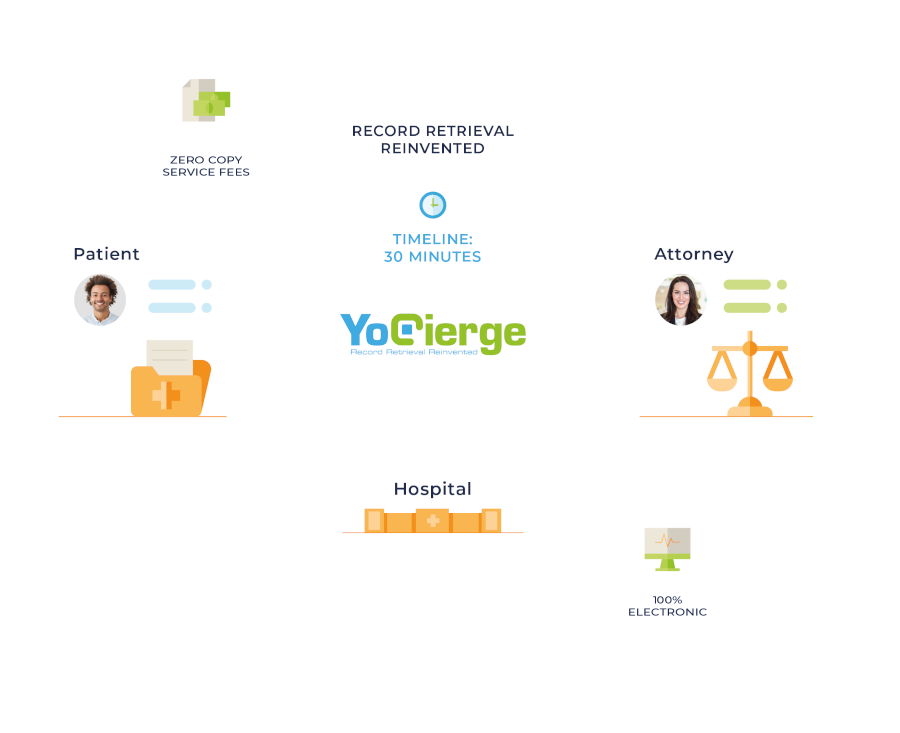
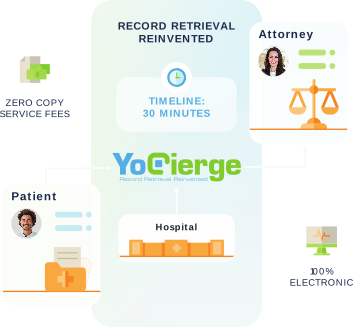
In order to design and implement effective security solutions, we develop an understanding of your infrastructure including long- and short-term goals, the capacity for resources, strengths and weaknesses, and your preferences regarding technology.
YoCierge leverages our years of experience implementing solutions to guarantee the best possible service to your organization. Our professionally certified engineers understand the process of setting objectives, engaging all stakeholders, managing expectations, and maintaining clear communications in order to deliver the best in integrated security solutions.
Security Solution Deployment
The correct technology solution has a tremendous impact on information security risk. At YoCierge, we practice a vendor-agnostic approach when considering solutions to serve our customer’s interests to the fullest degree. We continuously test new and existing solutions to provide accurate product information, and we are uniquely positioned to inform your organization regarding the best solutions for your needs and business objectives.
Comprehensive Project Execution
At YoCierge, our focus is on providing a business-centered approach to your specific technology implementation project. We achieve project success by establishing business and technical requirements at the beginning, including use cases, testing, and training requirements. We offer the best solutions for managing multiple project stakeholders in challenging client environments.
Security Tool Selection
YoCierge professionals continuously test and evaluate new and existing solutions so we can recommend and provide accurate product information to meet every need in your organization. As a vendor-agnostic technology partner, we are uniquely positioned to advise your organization on the needs and best solutions for your situation.